

Fig. 1. Fitbit system components: tracker, base, and laptop.
Fig. 2. Outcome of tracker injection (TI) attack on Fitbit
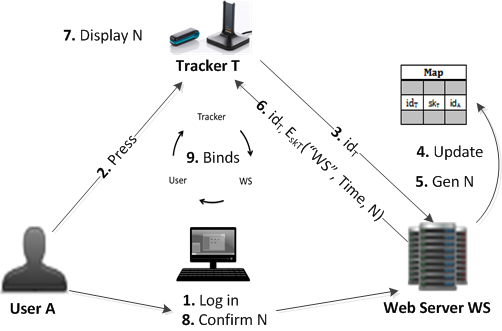
Fig. 3. The BindTrackerUser protocol between the user, tracker and the web server
The fusion of social networks and wearable sensors is becoming increasingly popular, with systems like Fitbit automating the process of reporting and sharing user fitness data. In this paper we show that while compelling, the careless integration of health data into social networks is fraught with privacy and security vulnerabilities. Case in point, by reverse engineering the communication protocol, storage details and operation codes, we identified several vulnerabilities in Fitbit. We have built FitBite, a suite of tools that exploit these vulnerabilities to launch a wide range of attacks against Fitbit. Besides eavesdropping, injection and denial of service, several attacks can lead to rewards and financial gains. We have built FitLock, a lightweight defense system that protects Fitbit while imposing only a small overhead. Our experiments on BeagleBoard and Xperia devices show that FitLock's end-to-end overhead over Fitbit is only 2.4%
| |
|
Fig. 1. Fitbit system components: tracker, base, and laptop. | Fig. 2. Outcome of tracker injection (TI) attack on Fitbit | Fig. 3. The BindTrackerUser protocol between the user, tracker and the web server |
We implemented FitLock in Android. We have tested the tracker side of FitLock on a Revision C4 of the BeagleBoard and an Xperia smartphone. In addition, we have used two Dell laptops, one equipped with a 2.4GHz Intel Core i5 and 4GB of RAM, was used for the web server (built on the Apache web server 2.4) and the other, equipped with a 2.3GHz Intel Core i5 and 4GB of RAM, was used for the base. We implemented a client-server Bluetooth socket communication protocol between the tracker (Xperia smartphone) and the base using PyBluez python library. FitBite was implemented on Ubuntu OS using ANT and libfitbit library.
To exploit the vulnerabilities to attack Fitbit , you can download:
To secure the Fitbit system, you can download: