Automated Derivation of Data Invariants for System Runtime Integrity Monitoring
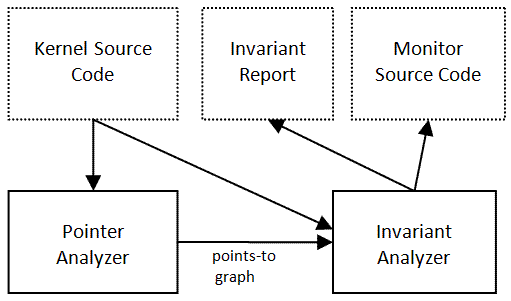
The recent interest in runtime attestation requires modeling of a program’s runtime behavior to formulate its integrity properties. We propose scoped invariants as a primitive for analyzing a software system for its integrity properties, and we develop automated tools that can derive scoped invariants for any given program: the first is a dynamic analysis tool that runs the target program in the QEMU machine emulator and monitors memory writes and events generated by the target program [3], and the second is a static analysis based tool that is field-sensitive, array-sensitive, and capable of handling pointers [1, 2]. We have applied our tools to Xen [3], the Linux kernel [2], and the Windows Research Kernel [1], which shows that static analysis is a viable option for automated integrity property derivation, and it can have very low false positive rate (1 out of 141,280 in our Linux kernel case study) and very low false negative rate (about 0.013%).
Papers:
Static analysis result download: we have applied the invariant analyzer above to a merged Linux kernel 2.4.32; you can click here to see a snippte of the generated analysis report, and here to download the entire report (905 KB). Note that the report is very large after decompression, so if you try to open it in a browser, it may take a long time. We suggest that you save the report and then use a text editor to read it.